Security Advisory
This document addresses an authentication bypass vulnerability in ManageEngine Endpoint DLP Plus and elaborates an incident response plan if your system is affected.
Severity: Critical
Update Release Date: 3rd December 2021
Fix Build:-
For Enterprise:
For builds 10.1.2134.1 and below, upgrade to 10.1.2134.2
What was the problem?
An authentication bypass vulnerability in ManageEngine Endpoint DLP Plus was identified and the vulnerability can allow an adversary to bypass authentication and execute arbitrary code in the Endpoint DLP Plus server.
How do I check if my installation is affected?
We have developed an Exploit Detection Tool that will help you identify whether your installation has been affected by this vulnerability. You can download the tool here. Once you have downloaded the file, follow these steps:
- Extract the tool to \ManageEngine\UEMS_CentralServer\bin folder or \ManageEngine\DesktopCentral_Server\bin folder, whichever is applicable for you.
- Open command prompt with admin privilege and navigate to \ManageEngine\UEMS_CentralServer\bin folder or \ManageEngine\DesktopCentral_Server\bin folder.
- Run the command RCEScan.bat
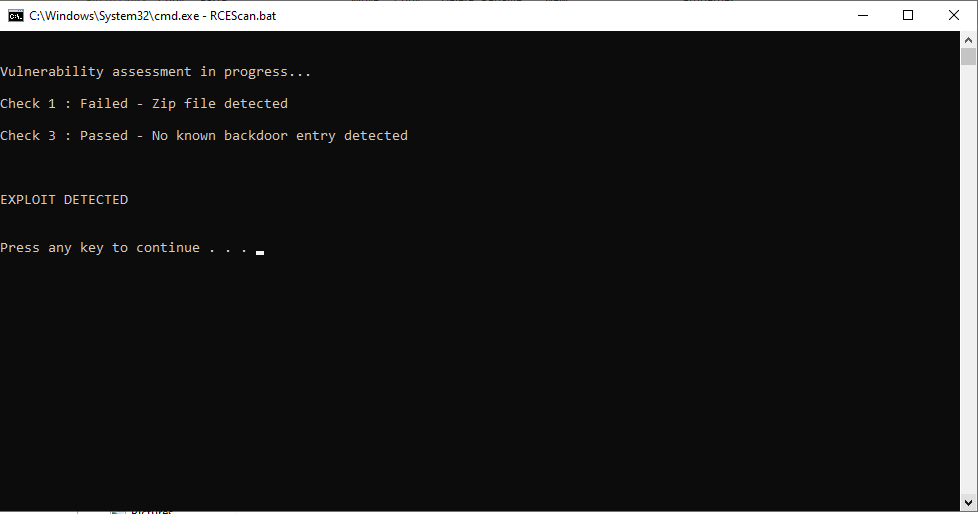
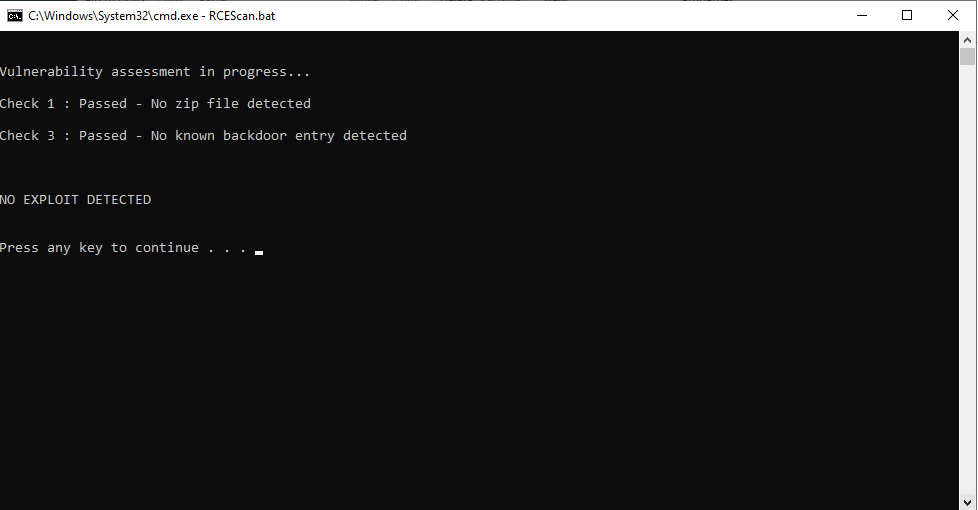
- As shown in the screenshots below, if your installation is affected, you will be thrown the message "Compromised". If your installation is unaffected, you will receive the message "Not Compromised".
Incident Response Plan
If affected:
1. Disconnect the affected system from your network.
2. Back up the Endpoint DLP Plus database using these steps.
3. Format the compromised machine. Note: Before formatting the machine, ensure that you have backed up all critical business data.
4. Follow these steps to restore Endpoint DLP Plus.
- The build version of the new installation should be the same as that of the database backup taken in step 2.
- It is highly recommended to utilize a different machine for the new installation.
5. Mandatory: Once the server is up and running, update Endpoint DLP Plus to the latest build using the following steps:
i) Log in to your Endpoint DLP Plus console, click on your current build number on the top right corner.
ii) You can find the latest build. Download the PPM and update.
Recommendation: Initiate a password reset for all services, accounts, Active Directory, etc. that has been accessed from the service installed machine. It is better if AD administrator passwords are also reset.
If not affected:
Update Endpoint DLP Plus to the latest build using the following steps:
i) Log in to your Endpoint DLP Plus console, click on your current build number on the top right corner. ii) You can find the latest build. Download the PPM and update.
For further assistance, please contact desktopcentral-security@manageengine.com
Keywords: Security Updates, Vulnerabilities and Fixes, authentication bypass